This is a quick post on how to perform NAT overload (PAT) towards a specific host only. I have an inside network of 10.10.1.0/24. I need a host in this network to reach the host 192.168.0.1. They don’t have direct connectivity so I need to PAT it behind the router which has an IP of 192.168.128.103. I don’t want to PAT all the traffic from 10.10.1.0/24, though, only towards this specific host. There are hosts in 192.168.128.0/24 that the VM should access using its original source. The network is shown in the diagram below:
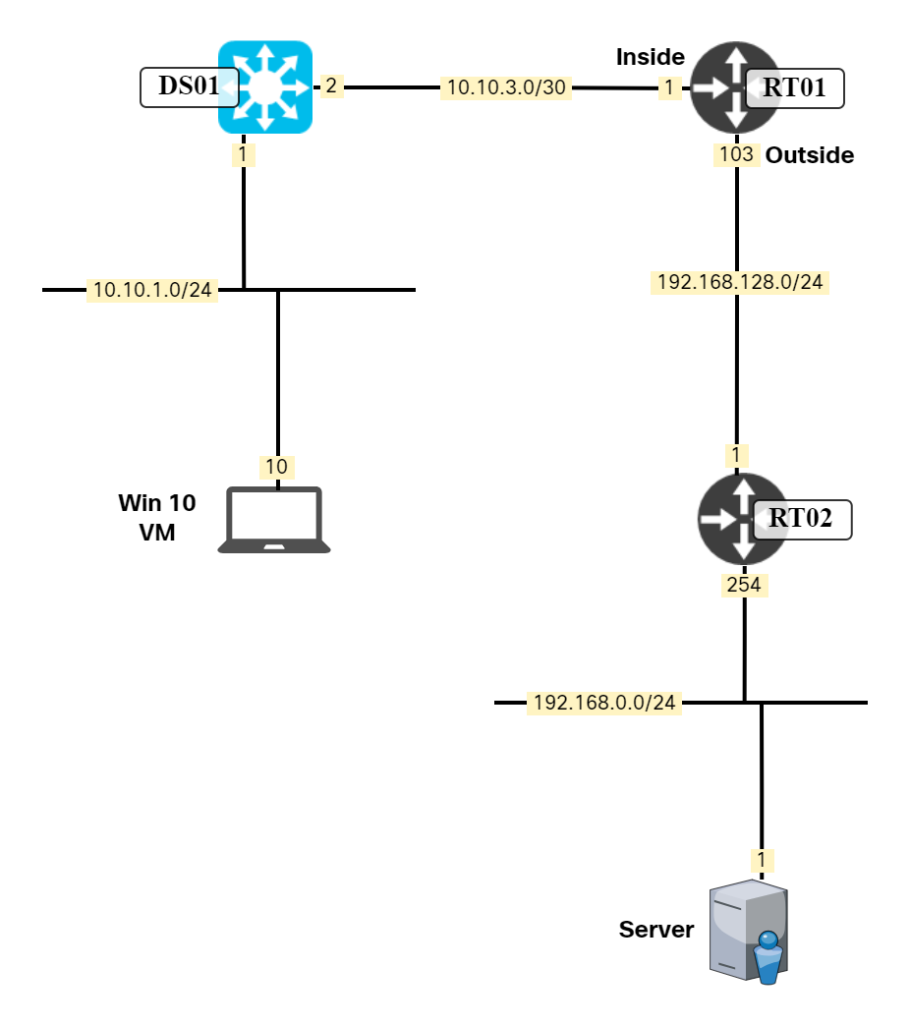
First, I’ll define my inside and outside interface:
RT01(config)#int gi0/0 RT01(config-if)#ip nat inside RT01(config-if)#int gi0/1 RT01(config-if)#ip nat outside
Then I’m going to create the ACL that matches on traffic from the 10.10.1.0/24 network to the host 192.168.0.1:
RT01(config)#ip access-list extended NAT-SRC-10.10.1.0/24 RT01(config-ext-nacl)#permit ip 10.10.1.0 0.0.0.255 host 192.168.0.1
Then, I’ll configure the NAT statement to match on the ACL and do an overload to interface Gi0/1:
RT01(config)#ip nat inside source list NAT-SRC-10.10.1.0/24 interface gi0/1 overload
Once the packets hit the router, it starts translating the packets:
RT01#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 192.168.128.103:1 10.10.1.10:1 192.168.0.1:1 192.168.0.1:1 tcp 192.168.128.103:49756 10.10.1.10:49756 192.168.0.1:1688 192.168.0.1:1688
There’s not more to it than that. To summarize, first enable NAT on your inside and outside interface, create an ACL matching on source network to specific destination host, configure NAT to overload to the interface based on the source access list.
Looks like there is a typo in the permit statement, Isnt it 10.10.1.0?
You are correct! Thanks! I’ve updated it now.
Should the wildcard not be 0.0.0.255 for a /24 subnet?
Indeed! Thanks, Rob!