Recently a posted a question to Twitter about connecting two Cisco Catalyst switches. One switch has already booted and has the following configuration:
interface GigabitEthernet0/0 description SW02 switchport mode trunk switchport trunk allowed vlan 1,10,20,30 switchport nonegotiate
The other switch is connected to Gi1/0/48 and has just been powered on. It has no configuration so it is booting with the default configuration. The intention is to onboard a new switch via Catalyst Center using Plug and Play (PNP).
Based on the responses not many people were able to describe what would happen and why or why not this scenario would work. There are some interesting details here and before running into this scenario myself I thought that it might work. Before we can answer if it will work, let’s list what we know at this point in time about the two switches, SW01, and SW02. For SW01 we know that:
- The port is configured as a trunk.
- The VLANs allowed on the trunk are 1,10,20, and 30.
- DTP has been disabled.
- The native VLAN is 1.
For SW02 we know that:
- It will boot with all ports enabled.
- Those ports will be in VLAN 1.
- DTP is enabled on the ports.
Now, since with the current configuration SW02’s port to SW01 will come up as an access port in VLAN 1, I considered that this could work since SW01’s port to SW02 is a trunk with native VLAN 1. In theory, SW02 would send untagged frames to SW01 and since native VLAN is 1 then those frames would be forwarded in VLAN 1. SW01 would send untagged frames in VLAN 1 to SW02 and there would be bidirectional flow of frames. This is correct in theory, but this is not what will happen. Why? Let’s take a look.
SW02#show int gi0/0 switchport Name: Gi0/0 Switchport: Enabled Administrative Mode: dynamic auto Operational Mode: static access Administrative Trunking Encapsulation: negotiate Operational Trunking Encapsulation: native Negotiation of Trunking: On Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none
SW02 is set to dynamic auto by default but other side has DTP disabled so port comes up as access port in VLAN 1. Let’s confirm with another command:
Protected: false Appliance trust: none SW02#show int gi0/0 trunk Port Mode Encapsulation Status Native vlan Gi0/0 auto negotiate not-trunking 1 Port Vlans allowed on trunk Gi0/0 1 Port Vlans allowed and active in management domain Gi0/0 1 Port Vlans in spanning tree forwarding state and not pruned Gi0/0 1
This may seem like it would work but then a message is logged to the console:
*Dec 9 07:10:32.320: %SPANTREE-7-RECV_1Q_NON_TRUNK: Received 802.1Q BPDU on non trunk GigabitEthernet0/0 VLAN1. *Dec 9 07:10:32.320: %SPANTREE-7-BLOCK_PORT_TYPE: Blocking GigabitEthernet0/0 on VLAN0001. Inconsistent port type.
What does this mean? It means that SW01 sent tagged STP BPDUs towards SW02. The message inconsistent port type explains what is going on. A trunk is connecting to an access port. To understand why this is happening, we need to go back to what type of BPDUs a Catalyst switch will generate as described in this Troubleshooting PVID inconsistencies by Cisco TAC. A Catalyst switch will generate the following BPDUs if the native VLAN is 1:
- Untagged BPDU for VLAN 1 sent to IEEE STP MAC address of 0180.c200.0000.
- Untagged BPDU for VLAN 1 sent to PVST+ MAC address of 0100.0ccc.cccd
- Tagged BPDU for non VLAN 1 sent to PVST+ MAC address of 0100.0ccc.cccd.
Why does Catalyst switches generate two BPDUs for VLAN1 or what the current native VLAN is? This is because Cisco runs Per VLAN Spanning Tree, but is also compatible with the IEEE standard of STP that is not operating per VLAN.
How is then the port inconsistency detected? This is because Cisco’s BPDU has a field that contains the originating VLAN of the BPDU:
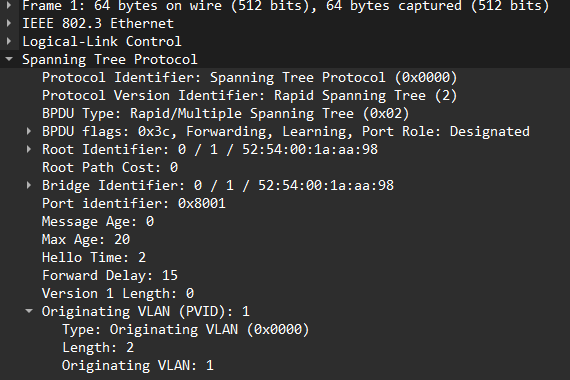
Even though the frame was sent untagged, the originating VLAN in th BPDU tells us that this is a trunk. SW02 on the other hand is only sending BPDUs to IEEE STP MAC address as it is an access port:
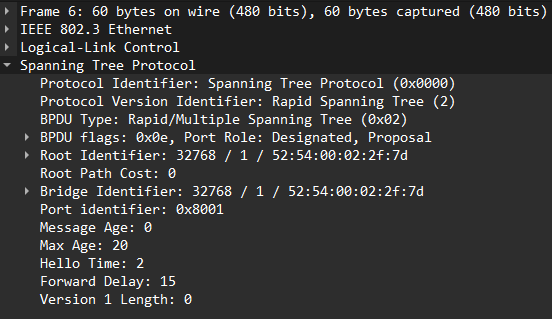
We can confirm on SW02 that we do have an inconsistent port:
SW02#show span inconsistentports Name Interface Inconsistency -------------------- ------------------------ ------------------ VLAN0001 GigabitEthernet0/0 Port Type Inconsistent Number of inconsistent ports (segments) in the system : 1
Note that the port is still up, though:
SW02#show int gi0/0
GigabitEthernet0/0 is up, line protocol is up (connected)
Hardware is iGbE, address is 5254.0002.2f7d (bia 5254.0002.2f7d)
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Auto Duplex, Auto Speed, link type is auto, media type is RJ45
output flow-control is unsupported, input flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of "show interface" counters never
Input queue: 3/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 1000 bits/sec, 2 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
733 packets input, 52654 bytes, 0 no buffer
Received 729 broadcasts (729 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 729 multicast, 0 pause input
396 packets output, 32042 bytes, 0 underruns
0 output errors, 0 collisions, 3 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
We can see some more details by looking at STP:
SW02#show span int gi0/0 Vlan Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- VLAN0001 Desg BKN*4 128.1 P2p *TYPE_Inc SW02#show span int gi0/0 det Port 1 (GigabitEthernet0/0) of VLAN0001 is broken (Port Type Inconsistent) Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 32769, address 5254.0002.2f7d Designated bridge has priority 32769, address 5254.0002.2f7d Designated port id is 128.1, designated path cost 0 Timers: message age 0, forward delay 13, hold 0 Number of transitions to forwarding state: 0 Link type is point-to-point by default BPDU: sent 71, received 71
Note the number of BPDUs sent and received. In a stable topology there would be more BPDUs either sent or received depending on what side of the link is Designated. In this scenario, there is not a stable topology due to the inconsistency so both sides keep sending BPDUs as they believe they are Designated.
So from a data plane perspective it would be possible for trunk with native VLAN 1 connecting to access port in VLAN 1 to work, the control plane is preventing us from doing so as port inconsistency is generally a bad thing meaning that something has been misconfigured.
You may recall that we had several VLANs on the trunk. What would happen if we only allowed VLAN 1?
interface GigabitEthernet0/0 switchport trunk allowed vlan 1 switchport mode trunk switchport nonegotiate
The outcome would still be the same as SW01 is originating BPDUs with VLAN information in it. The following is logged on SW02:
*Dec 9 07:35:43.405: %SPANTREE-7-RECV_1Q_NON_TRUNK: Received 802.1Q BPDU on non trunk GigabitEthernet0/0 VLAN1. *Dec 9 07:35:43.406: %SPANTREE-7-BLOCK_PORT_TYPE: Blocking GigabitEthernet0/0 on VLAN0001. Inconsistent port type.
Right, so how do we get to a stable topology? How about enabling DTP on SW01?
SW01#conf t Enter configuration commands, one per line. End with CNTL/Z. SW01(config)#int gi0/0 SW01(config-if)#no switchport nonegotiate
What will then happen to the port of SW02?
SW02#show int gi0/0 switchport Name: Gi0/0 Switchport: Enabled Administrative Mode: dynamic auto Operational Mode: trunk Administrative Trunking Encapsulation: negotiate Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none
It’s now a trunk port! This is because one side is dynamic auto and the other is trunk so a trunk is formed on SW02. The inconsistency is now gone:
SW02#show span inconsistentports Name Interface Inconsistency -------------------- ------------------------ ------------------ Number of inconsistent ports (segments) in the system : 0
This is also confirmed by looking at STP output:
SW02#show span int gi0/0 Vlan Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- VLAN0001 Root FWD 4 128.1 P2p SW02#show span int gi0/0 det Port 1 (GigabitEthernet0/0) of VLAN0001 is root forwarding Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 1, address 5254.001a.aa98 Designated bridge has priority 1, address 5254.001a.aa98 Designated port id is 128.1, designated path cost 0 Timers: message age 16, forward delay 0, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 4, received 49
Great! Problem solved! Now, what would happen if we change the native VLAN to something else than 1 on SW01?
SW01(config)#int gi0/0 SW01(config-if)#switchport trunk native vlan 10 SW01(config-if)#
The following messages can be see in the log of SW01:
*Dec 9 07:21:24.939: %SPANTREE-2-RECV_PVID_ERR: Received BPDU with inconsistent peer vlan id 1 on GigabitEthernet0/0 VLAN10. *Dec 9 07:21:24.939: %SPANTREE-2-BLOCK_PVID_PEER: Blocking GigabitEthernet0/0 on VLAN0001. Inconsistent peer vlan. *Dec 9 07:21:24.940: %SPANTREE-2-BLOCK_PVID_LOCAL: Blocking GigabitEthernet0/0 on VLAN0010. Inconsistent local vlan. *Dec 9 07:22:14.563: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on GigabitEthernet0/0 (10), with SW02 GigabitEthernet0/0 (1).
There is now a native VLAN mismatch! Note that CDP reports on the mismatch but the mismatch was discovered by receiving BPDU in VLAN 10 with an originating VLAN of 1:
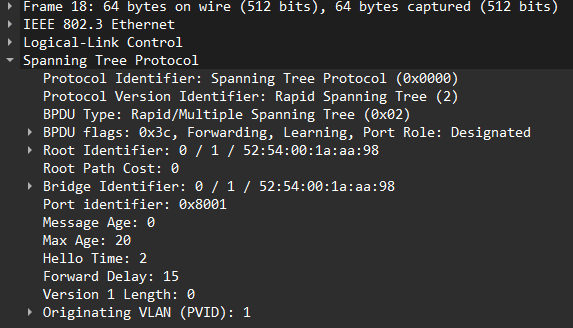
SW01 is blocking VLAN 1 and VLAN 10 as they are inconsistent:
SW01#show span inconsistentports Name Interface Inconsistency -------------------- ------------------------ ------------------ VLAN0001 GigabitEthernet0/0 Port VLAN ID Mismatch VLAN0010 GigabitEthernet0/0 Port VLAN ID Mismatch Number of inconsistent ports (segments) in the system : 2
Note that the other VLANs are allowed to forward, though:
SW01#show span int gi0/0 Vlan Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- VLAN0001 Desg BKN*4 128.1 P2p *PVID_Inc VLAN0010 Desg BKN*4 128.1 P2p *PVID_Inc VLAN0020 Desg FWD 4 128.1 P2p VLAN0030 Desg FWD 4 128.1 P2p SW01#show span int gi0/0 det Port 1 (GigabitEthernet0/0) of VLAN0001 is broken (Port VLAN ID Mismatch) Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 1, address 5254.001a.aa98 Designated bridge has priority 1, address 5254.001a.aa98 Designated port id is 128.1, designated path cost 0 Timers: message age 0, forward delay 14, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 219, received 110 Port 1 (GigabitEthernet0/0) of VLAN0010 is broken (Port VLAN ID Mismatch) Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 10, address 5254.001a.aa98 Designated bridge has priority 10, address 5254.001a.aa98 Designated port id is 128.1, designated path cost 0 Timers: message age 0, forward delay 14, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 219, received 0 Port 1 (GigabitEthernet0/0) of VLAN0020 is designated forwarding Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 20, address 5254.001a.aa98 Designated bridge has priority 20, address 5254.001a.aa98 Designated port id is 128.1, designated path cost 0 Timers: message age 0, forward delay 0, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 219, received 0 Port 1 (GigabitEthernet0/0) of VLAN0030 is designated forwarding Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 30, address 5254.001a.aa98 Designated bridge has priority 30, address 5254.001a.aa98 Designated port id is 128.1, designated path cost 0 Timers: message age 0, forward delay 0, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 219, received 0
Similarly, SW02 is also blocking:
*Dec 9 07:21:24.266: %SPANTREE-2-RECV_PVID_ERR: Received BPDU with inconsistent peer vlan id 10 on GigabitEthernet0/0 VLAN1. *Dec 9 07:21:24.268: %SPANTREE-2-BLOCK_PVID_LOCAL: Blocking GigabitEthernet0/0 on VLAN0001. Inconsistent local vlan. *Dec 9 07:21:57.891: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on GigabitEthernet0/0 (1), with SW01 GigabitEthernet0/0 (10).
When the correct native VLAN is configured the inconsistency is resolved. Log message on SW01:
*Dec 9 07:33:44.054: %SPANTREE-2-UNBLOCK_CONSIST_PORT: Unblocking GigabitEthernet0/0 on VLAN0001. Port consistency restored. *Dec 9 07:33:44.055: %SPANTREE-2-UNBLOCK_CONSIST_PORT: Unblocking GigabitEthernet0/0 on VLAN0010. Port consistency restored.
Log message on SW02:
*Dec 9 07:33:43.859: %SPANTREE-2-UNBLOCK_CONSIST_PORT: Unblocking GigabitEthernet0/0 on VLAN0001. Port consistency restored.
That’s a lot of details in this post but I hope it helped clarify some of the STP concepts and detection of misconfiguration. What did we learn? We learned that:
- Catalyst switches boot with all ports in VLAN 1 and with DTP enabled.
- Ports will be dynamic auto by default and will form a trunk if the other side is a trunk as long as DTP has not been disabled.
- While trunk connected to access port may work from data plane perspective, control plane detects the misconfiguration.
- Cisco switches sends BPDUs to both IEEE MAC address as well as Cisco’s MAC address.
- Cisco’s BPDU has information about the originating VLAN.
- While CDP reports on misconfiguration of native VLAN, it is STP that is detecting the misconfiguration.
Thanks for reading!
Nice one Daniel.. I followed through to see this answer from twitter after seeing your quiz.. Thanks alot
Thanks!
DTP might been glossed as (cisco proprietary) dynamic trunking protocol for readers like me who might have dealt with the same concepts but in a non-Cisco context.
Still an interesting read in spite of a detour to look up DTP.