Yesterday I showed how to bootstrap a Catalyst8000v from the CLI. Today, I will show how to put a file on bootflash which includes the configuration but also the root certificate and the certificate of the device. This is a bit of a more streamlined process and can also be useful if you don’t know what CLI commands to use as vManage will generate the configuration for you.
Starting out, we have a freshly booted router that is in autonomous mode (non-SD-WAN):
Router#sh ver | i operating Router operating mode: Autonomous
To generate the bootstrap configuration, the process is to first go through the regular process of attaching a device to a template. Go to Configuration -> Templates and select Attach Devices:
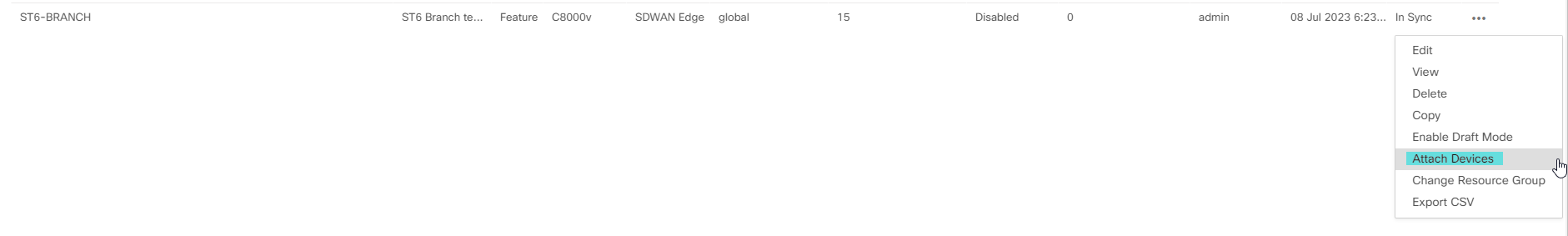
Select the correct device:
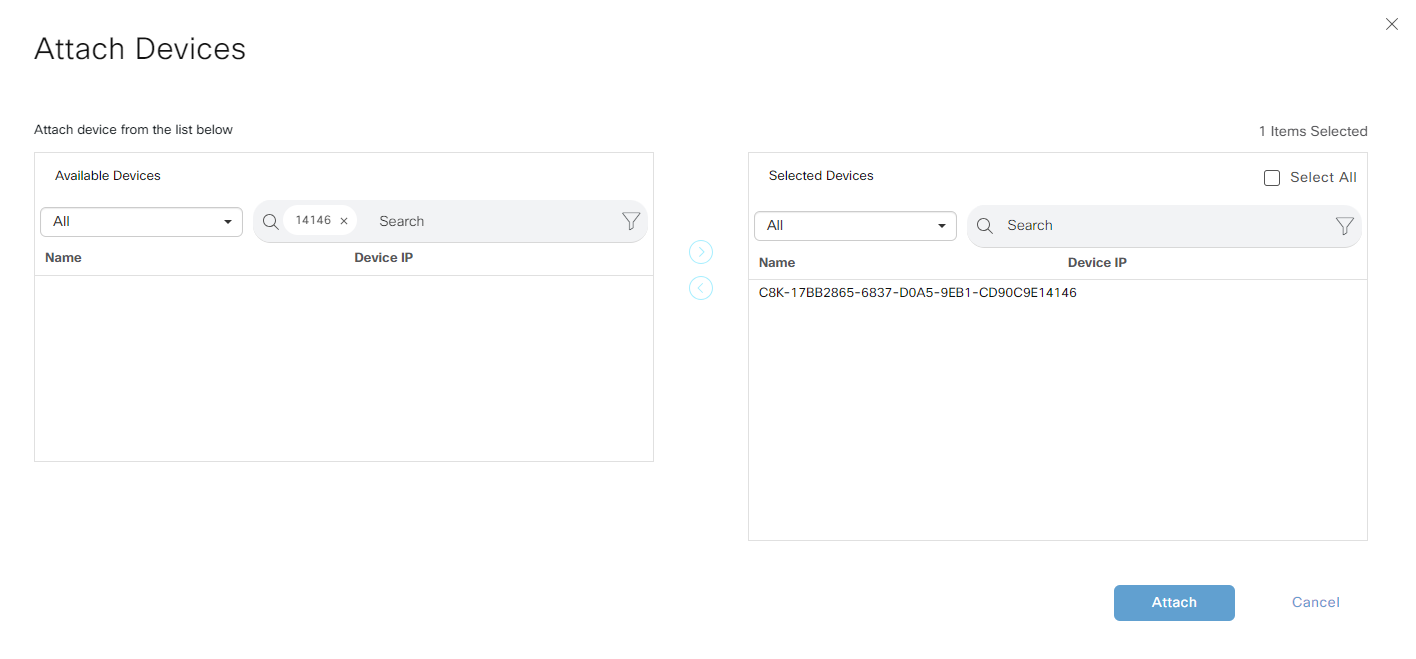
Fill in the information needed:
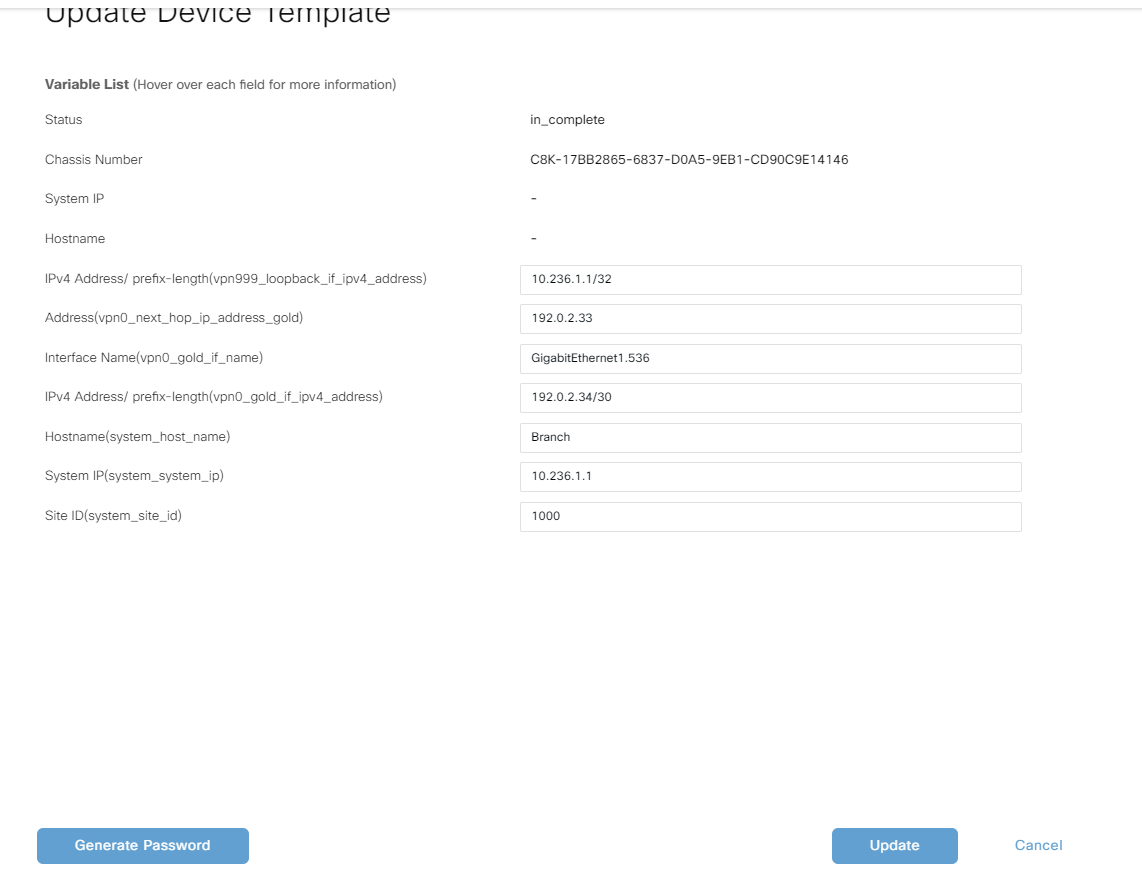
Click Update to reflect the edits:
Then click Next:
Click Configure Devices and vManage will try to push the config but the device is offline:
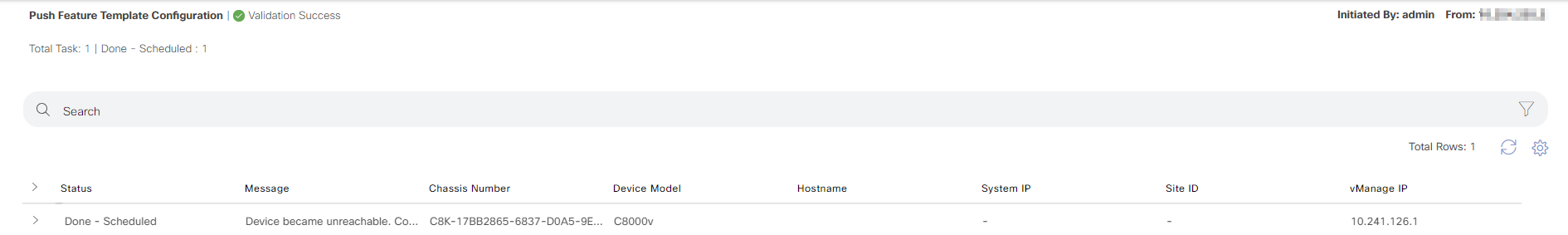
Once this is done, vManage has all the information it needs to generate the bootstrap. Go to Configuration -> Devices and select the correct device and then Generate Bootstrap Configuration:
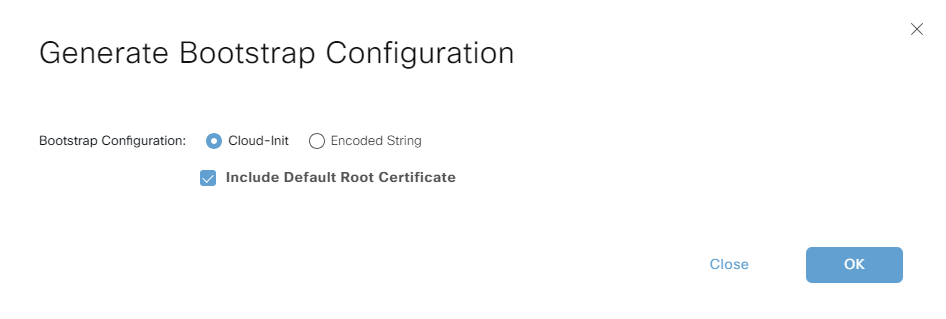
Then vManage will disply the following window. Choose Cloud-Init and have the box selected to Include Default Root Certificate:
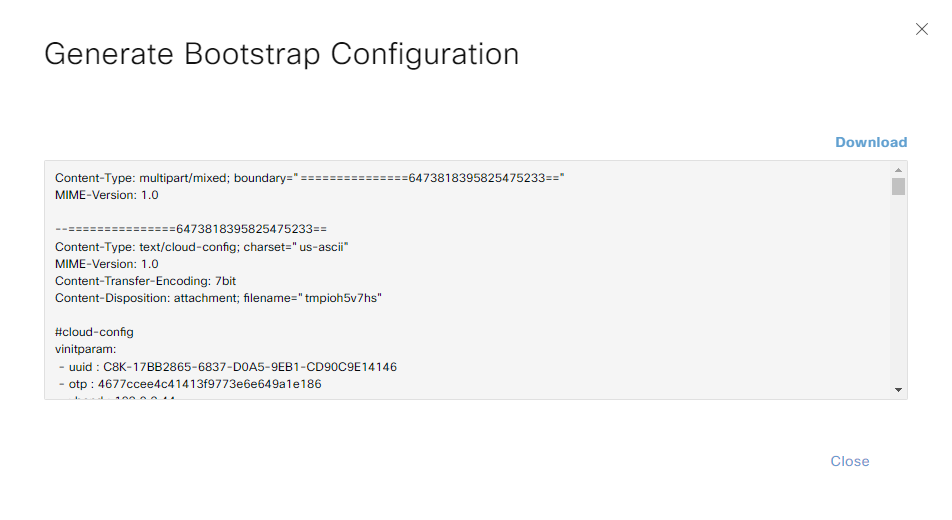
Click OK and vManage will generate the entire bootstrap configuration, including root certificate and certificate:
When generating the bootstrap configuration, I recommend to use a simplified template only used for onboarding. Don’t include the full configuration as that means there is more potential for errors in the config. I did for example run into a problem regarding how subinterfaces are handled where I had used a template using the newer way of doing it, but where the router was shipped with older code so my bootstrap configuration could not be applied to the device.
The bootstrap configuration will be named something like C8K-17BB2865-6837-D0A5-9EB1-CD90C9E14146.cfg and look something like this:
Content-Type: multipart/mixed; boundary="===============6473818395825475233=="
MIME-Version: 1.0
--===============6473818395825475233==
Content-Type: text/cloud-config; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
Content-Disposition: attachment; filename="tmpioh5v7hs"
#cloud-config
vinitparam:
- uuid : C8K-17BB2865-6837-D0A5-9EB1-CD90C9E14146
- otp : 4677ccee4c41413f9773e6e649a1e186
- vbond : 192.0.2.44
- org : sd-wan-lab-daniel
- rcc : true
ca-certs:
remove-defaults: false
trusted:
- |
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
Snip
-----END CERTIFICATE-----
--===============6473818395825475233==
Content-Type: text/cloud-boothook; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
Content-Disposition: attachment; filename="config-C8K-17BB2865-6837-D0A5-9EB1-CD90C9E14146.txt"
#cloud-boothook
system
ztp-status success
pseudo-confirm-commit 300
personality vedge
device-model vedge-C8000V
chassis-number C8K-17BB2865-6837-D0A5-9EB1-CD90C9E14146
system-ip 10.236.1.1
overlay-id 1
site-id 1000
no transport-gateway enable
port-offset 0
control-session-pps 300
admin-tech-on-failure
sp-organization-name sd-wan-lab-daniel
organization-name sd-wan-lab-daniel
port-hop
track-transport
track-default-gateway
console-baud-rate 9600
config-template-name ST6-BRANCH
no on-demand enable
on-demand idle-timeout 10
vbond 192.0.2.44 port 12346
logging
disk
enable
!
!
!
bfd default-dscp 48
bfd app-route multiplier 6
bfd app-route poll-interval 120000
security
ipsec
rekey 86400
replay-window 512
authentication-type sha1-hmac ah-sha1-hmac
integrity-type esp ip-udp-esp
!
!
sslproxy
no enable
rsa-key-modulus 2048
certificate-lifetime 730
eckey-type P256
ca-tp-label PROXY-SIGNING-CA
settings expired-certificate drop
settings untrusted-certificate drop
settings unknown-status drop
settings certificate-revocation-check none
settings unsupported-protocol-versions drop
settings unsupported-cipher-suites drop
settings failure-mode close
settings minimum-tls-ver TLSv1
dual-side optimization enable
!
sdwan
interface GigabitEthernet1.536
tunnel-interface
encapsulation ipsec weight 1
no border
color gold
no last-resort-circuit
no low-bandwidth-link
no vbond-as-stun-server
vmanage-connection-preference 5
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
appqoe
no tcpopt enable
no dreopt enable
no httpopt enable
!
omp
no shutdown
send-path-limit 16
ecmp-limit 8
graceful-restart
no as-dot-notation
timers
holdtime 60
advertisement-interval 1
graceful-restart-timer 43200
eor-timer 300
exit
address-family ipv4
advertise bgp
advertise connected
advertise static
!
address-family ipv6
advertise connected
advertise static
!
!
!
banner login Un authorised Logins tracked
banner motd Restricted Use
service tcp-keepalives-in
service tcp-keepalives-out
no service tcp-small-servers
no service udp-small-servers
hostname Branch
username admin privilege 15 secret 9 snip
vrf definition 100
description MAIN VRF
rd 1:100
address-family ipv4
route-target export 1:100
route-target import 1:100
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition 200
description MGMT VRF
rd 1:200
address-family ipv4
route-target export 1:200
route-target import 1:200
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition Mgmt-intf
description OOB_MGMT
rd 1:512
address-family ipv4
route-target export 1:512
route-target import 1:512
exit-address-family
!
address-family ipv6
exit-address-family
!
!
ip arp proxy disable
no ip finger
no ip rcmd rcp-enable
no ip rcmd rsh-enable
no ip dhcp use class
no ip ftp passive
ip route 0.0.0.0 0.0.0.0 192.0.2.33
ip bootp server
no ip source-route
no ip ssh bulk-mode
no ip http server
no ip http secure-server
no ip http ctc authentication
ip nat settings central-policy
interface GigabitEthernet1.536
description GOLD
no shutdown
arp timeout 1200
encapsulation dot1Q 536
ip address 192.0.2.34 255.255.255.252
no ip redirects
ip mtu 1500
exit
interface GigabitEthernet3
description OOB_IF
no shutdown
arp timeout 1200
vrf forwarding Mgmt-intf
ip address dhcp client-id GigabitEthernet3
no ip redirects
ip dhcp client default-router distance 1
ip mtu 1500
load-interval 30
mtu 1500
negotiation auto
exit
interface Loopback0
description MGMT_loopback
no shutdown
arp timeout 1200
vrf forwarding 200
ip address 10.236.1.1 255.255.255.255
no ip redirects
ip mtu 1500
exit
interface Tunnel536001
no shutdown
ip unnumbered GigabitEthernet1.536
no ip redirects
ipv6 unnumbered GigabitEthernet1.536
no ipv6 redirects
tunnel source GigabitEthernet1.536
tunnel mode sdwan
exit
clock timezone UTC 0 0
logging persistent size 104857600 filesize 10485760
no logging monitor
logging buffered 512000
logging console
aaa authentication login default local
aaa authorization exec default local
aaa server radius dynamic-author
!
no crypto ikev2 diagnose error
no crypto isakmp diagnose error
no network-clock revertive
snmp-server ifindex persist
fhrp version vrrp v2
line con 0
speed 9600
stopbits 1
!
line vty 0 4
transport input ssh
!
line vty 5 80
transport input ssh
!
lldp run
nat64 translation timeout tcp 3600
nat64 translation timeout udp 300
!
!
--===============6473818395825475233==--
This file needs to be uploaded to bootflash of the device, the same process can be used for HW devices and be stored on bootflash or more commonly USB device to not have to login to the device to apply the configuration. For the device to load the configuration, the file must be renamed to ciscosdwan.cfg for HW devices but ciscosdwan_cloud_init.cfg for SW devices.
Upload the file to bootflash of the device using for example FTP:
Router#copy ftp://user:password@ip/ciscosdwan_cloud_init.cfg bootflash: Destination filename [ciscosdwan_cloud_init.cfg]? Accessing ftp://*:*@ip/ciscosdwan_cloud_init.cfg...! [OK - 33708/4096 bytes] 33708 bytes copied in 0.337 secs (100024 bytes/sec) Router#dir bootflash: Directory of bootflash:/ 30 -rw- 33708 Jul 8 2023 05:10:22 +00:00 ciscosdwan_cloud_init.cfg
Now configure the device to be in controller mode (it should be able to detect mode based on the file but this didn’t work on my router):
Router#controller-mode enable Enabling controller mode will erase the nvram filesystem, remove all configuration files, and reload the box! Ensure the BOOT variable points to a valid image Continue? [confirm] % Warning: Bootstrap config file needed for Day-0 boot is missing Do you want to abort? (yes/[no]): no
Now verify that the root cert is there:
Branch#show sdwan certificate root-ca-cert | i sd-wan
Issuer: C = X, ST = X, L = X, O = sd-wan-lab-daniel, CN = vManage
Subject: C = X, ST = X, L = X, O = sd-wan-lab-daniel, CN = vManage
Verify that the device has a certificate:
Branch#show sdwan control local-properties personality vedge sp-organization-name sd-wan-lab-daniel organization-name sd-wan-lab-daniel root-ca-chain-status Installed root-ca-crl-status Not-Installed certificate-status Installed certificate-validity Valid certificate-not-valid-before Jul 8 06:11:21 2023 GMT certificate-not-valid-after Jul 5 06:11:21 2033 GMT enterprise-cert-status Not Applicable enterprise-cert-validity Not Applicable enterprise-cert-not-valid-before Not Applicable enterprise-cert-not-valid-after Not Applicable dns-name 192.0.2.44 site-id 1000 domain-id 1 protocol dtls tls-port 0 system-ip 10.236.1.1 chassis-num/unique-id C8K-17BB2865-6837-D0A5-9EB1-CD90C9E14146 serial-num 8FBCE3B3 subject-serial-num N/A enterprise-serial-num No certificate installed token Invalid keygen-interval 1:00:00:00 retry-interval 0:00:00:15 no-activity-exp-interval 0:00:00:20 dns-cache-ttl 0:00:00:00 port-hopped FALSE time-since-last-port-hop 0:00:00:00 embargo-check success device-role edge-router region-id-set N/A number-vbond-peers 1
Verify that control connections are up:
Branch#show sdwan control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION LOCAL COLOR PROXY STATE UPTIME ID
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 10.240.126.3 xxxxxxxxxx 1 192.0.2.43 12446 192.0.2.43 12446 sd-wan-lab-daniel gold No up 0:00:05:02 0
vsmart dtls 10.240.127.3 xxxxxxxxxx 1 192.0.2.51 12446 192.0.2.51 12446 sd-wan-lab-daniel gold No up 0:00:05:02 0
vmanage dtls 10.241.126.1 xxxxxxxxxx 0 192.0.2.42 13046 192.0.2.42 13046 sd-wan-lab-daniel gold No up 0:00:05:02 0
The advantage to using this type of bootstrap configuration is that it includes the root cert and certificate so there is no need to manually copy the root cert to the device or request to install a certificate. I hope this post has been useful in showing options in bootstrapping a device.