I recently ran into some limitations of IPv6 ACLs on the Catalyst 3750 platform. I had developed an ACL to protect from receiving traffic from unwanted address ranges such as ::, ::1, ::FFFF:0:0/96. The first address is the unspecified address, the second one is the loopback address and the last one is IPv4 mapped traffic. The ACL also contained an entry to deny traffic with routing-type 0.
Note that no error is output when adding the entries in the ACL, only when applying the ACL to an interface.
% This ACL contains following unsupported entries.
% Remove those entries and try again.
deny ipv6 any any routing-type 0 sequence 20
deny ipv6 host ::1 any sequence 290
deny ipv6 host :: any sequence 310
deny ipv6 ::FFFF:0.0.0.0/96 any sequence 330
% This ACL can not be attached to the interface.
SW1(config-if)#
%PARSE_RC-4-PRC_NON_COMPLIANCE: `ipv6 traffic-filter v6-ACL-IN in'
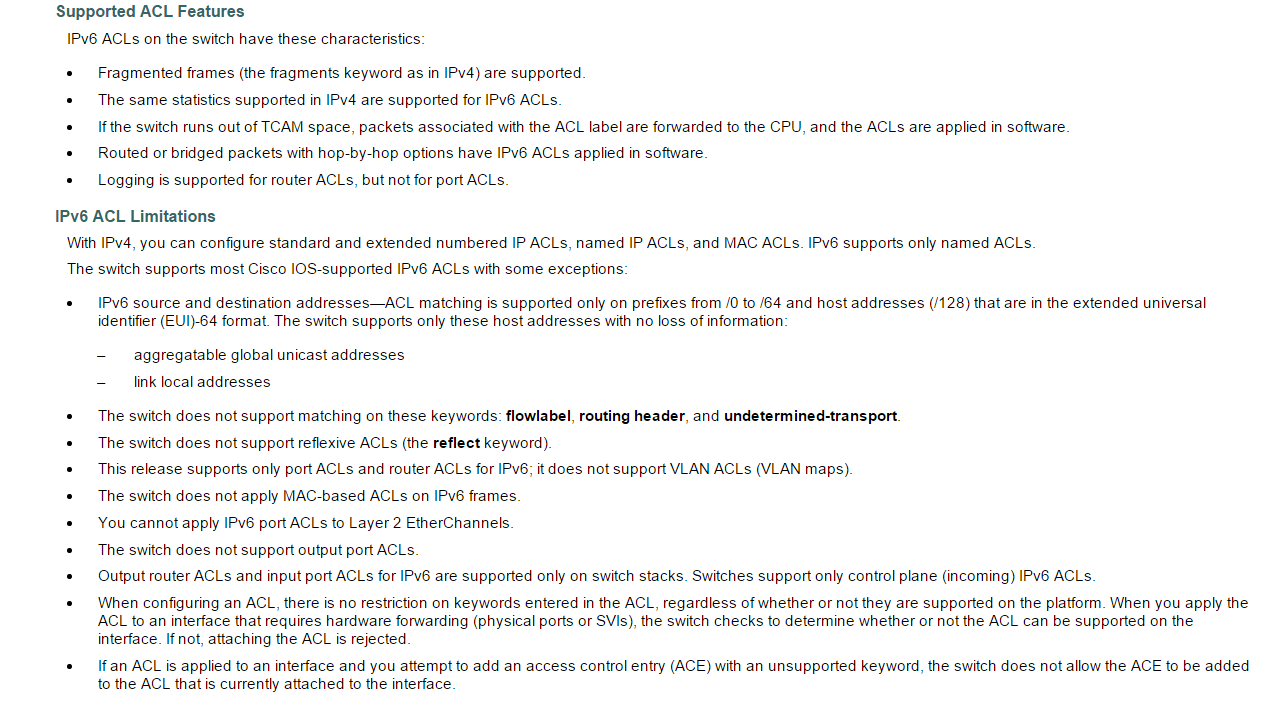
From the configuration guide, the following limitations apply to the Catalyst 3750 platform.
What this means is that we can’t match on flowlabel, routing-header and undetermined transport upper layer protocol. We also need to match on networks ranging from /0 to /64 and host addresses that are belonging to global unicast or link local.
I believe this is a limitation of the platform regarding how much TCAM space there is available. Because IPv6 addresses are 128 bits compared to 32 of IPv4, a lot more TCAM space is required to implement ACLs for IPv6.