Most ISE deployments use a join to Active Directory to be able to query AD groups, perform user lookups, etc. In this post, I’ll join my ISE lab server to AD. First I’m going to create two OUs in my AD, one for users and one for computers. Why not use the default ones? They are containers, not OUs, which means you can’t apply GPOs to them. Additionally, it makes for cleaner separation from the built-in accounts and allows for applying policies that won’t affect them. I’m creating two OUs:
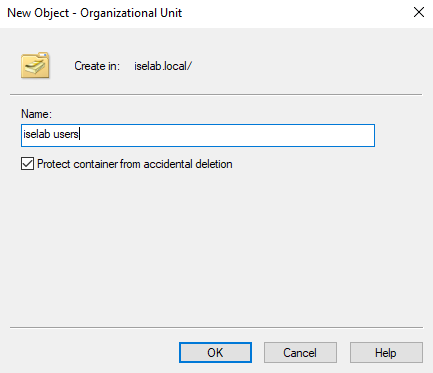
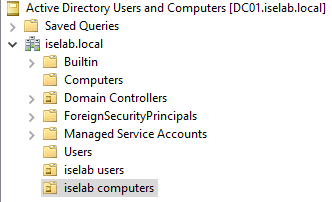
- iselab users.
- iselab computers.
This is done by going to Active Directory Users and Computers, then right clicking the AD domain and selecting New -> Organizational Unit:
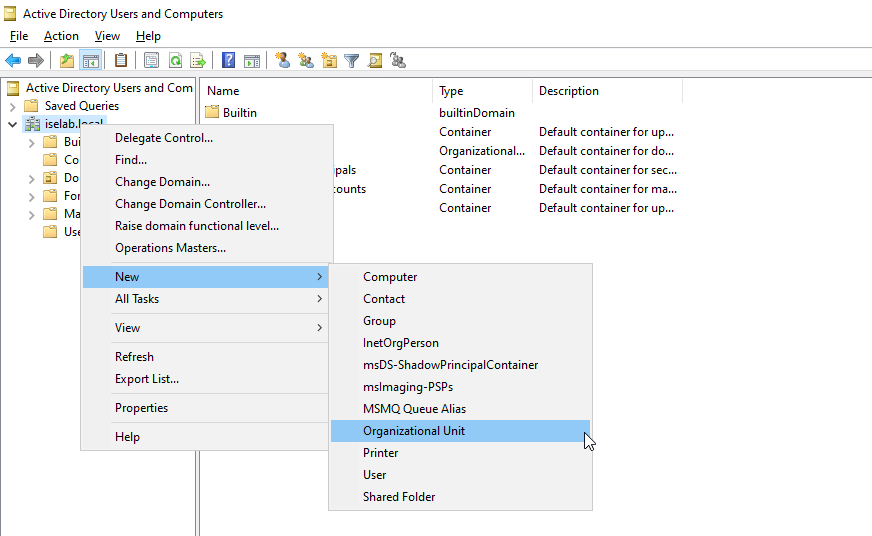
Give the OU a name and then click OK:
Repeat for the computers OU. You should now be able to see the OUs:
I’m going to create a user named Bob that I’ll be using to test login later. Right click the users OU and then select New -> User:
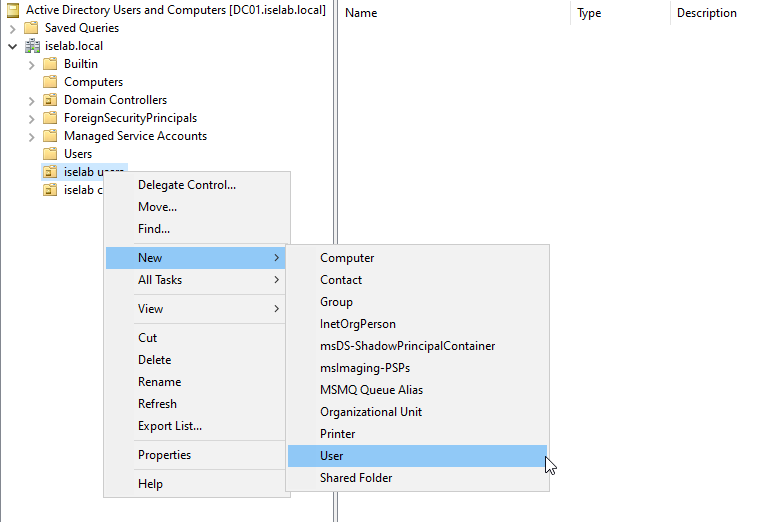
Enter the name and logon name:
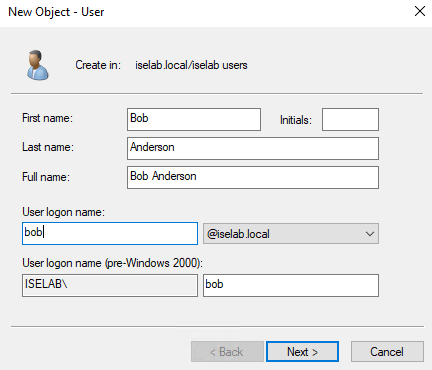
Click Next. Enter a password for the user. As this is a lab, I won’t require that the user changes the password and the password is set to not expire:
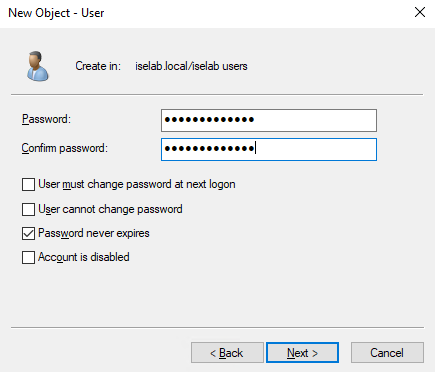
Click Next. Then click Finish. The user has been created:
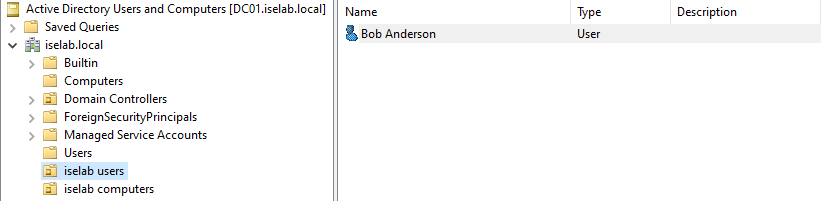
Now we’re going to join ISE to AD. We’ll need two things:
- AD domain name.
- AD account with privileges to search AD, create ISE machine account, and set attributes on the machine account.
Note that the credentials used to join the domain are only used once and that the credentials aren’t stored anywhere in ISE.
In ISE go to Administration -> External Identity Sources -> Active Directory. The list is currently empty:
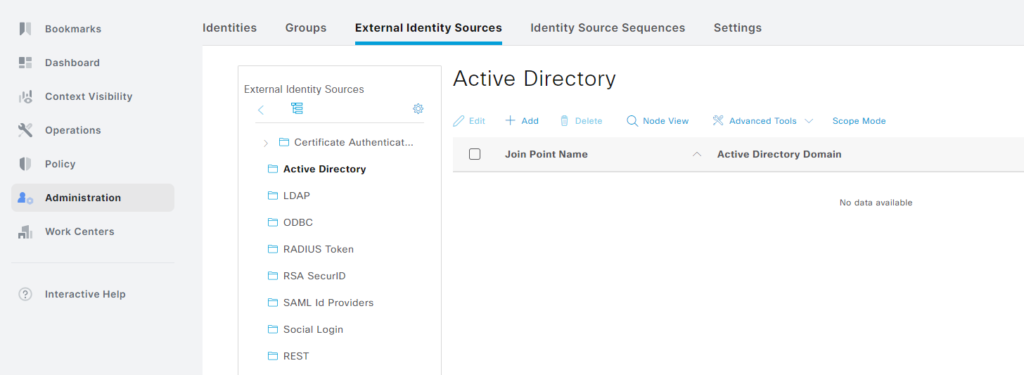
Click + Add and enter the Join Point Name and the AD domain:
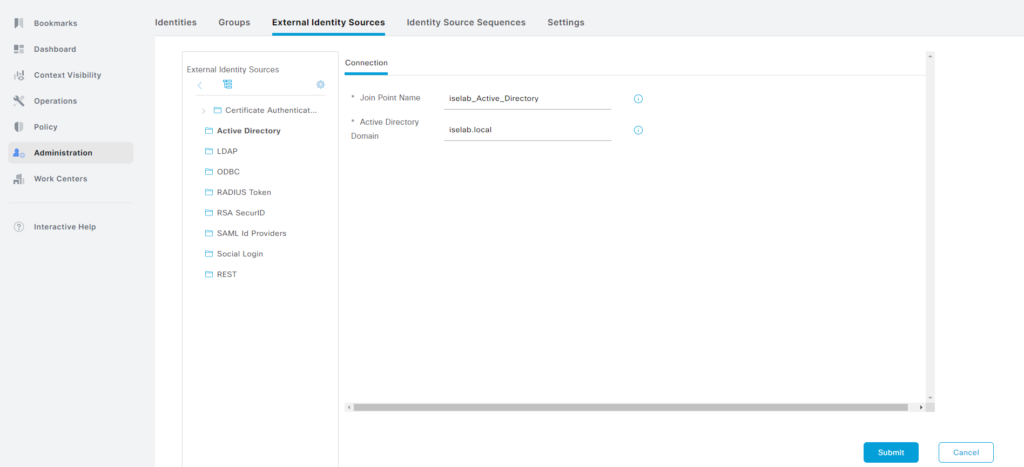
Click Submit. A popup appears asking if all nodes should be joined to the domain:
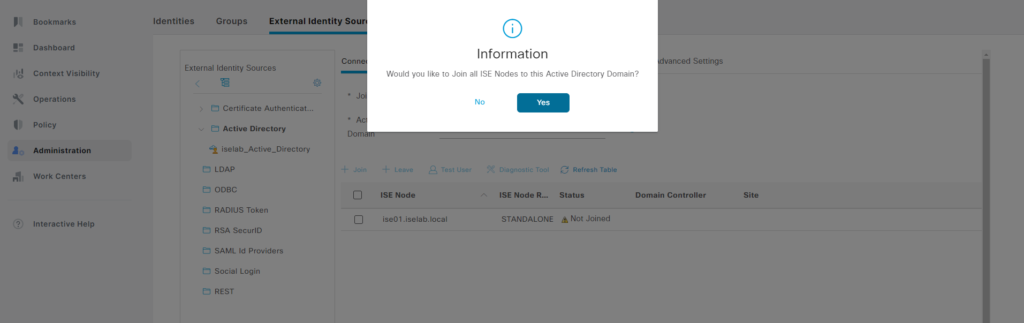
Select Yes. Enter credentials of account with privileges to join:
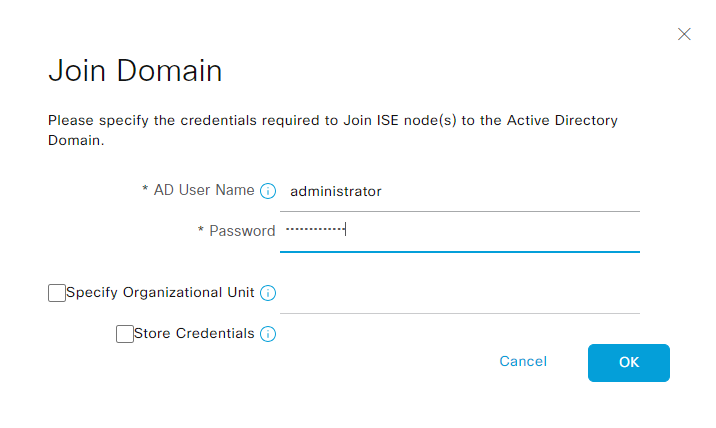
Click OK. The process is completed:
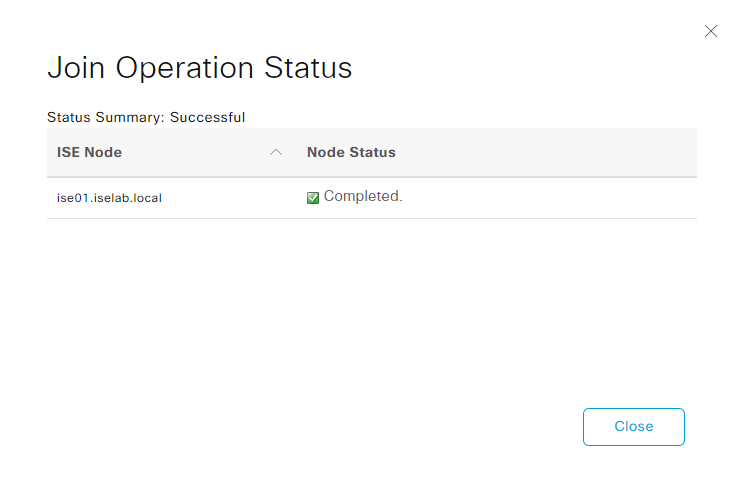
The AD join has been added:
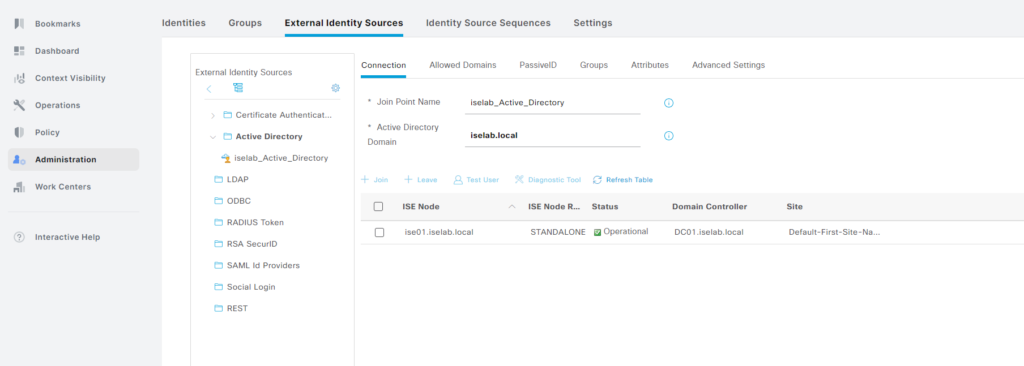
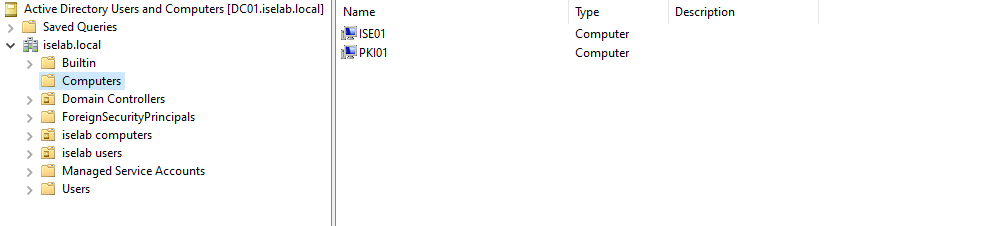
Going back to the AD console, there is now an account that has been created for ISE:
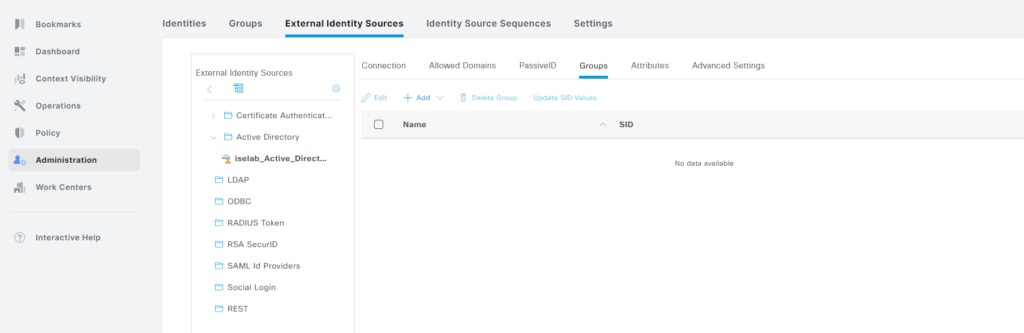
Finally, let’s import the OUs from AD that we created previously. Go to the Groups tab when your join point is selected:
Click + Add and then Select Groups from Directory:
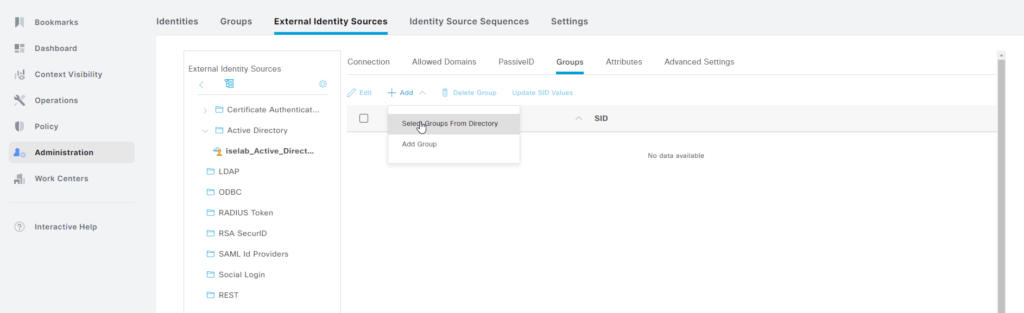
Click Retrieve Groups…
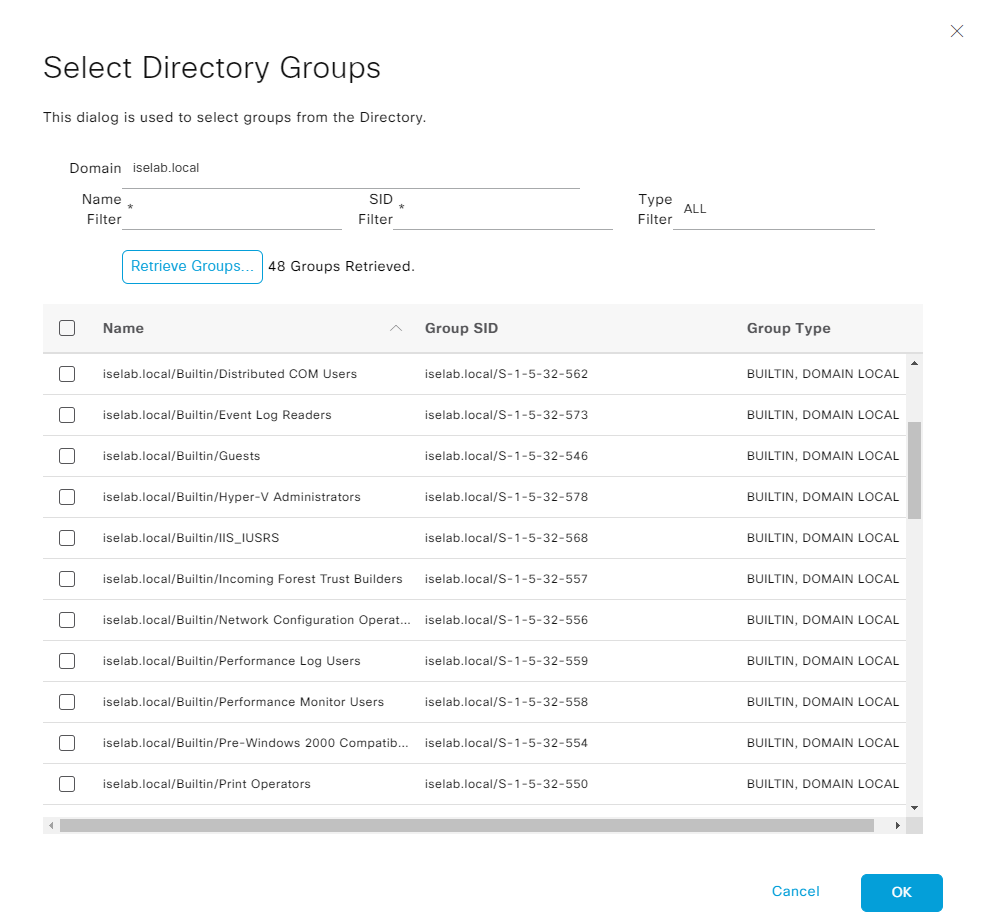
Then select the groups you want and click OK:
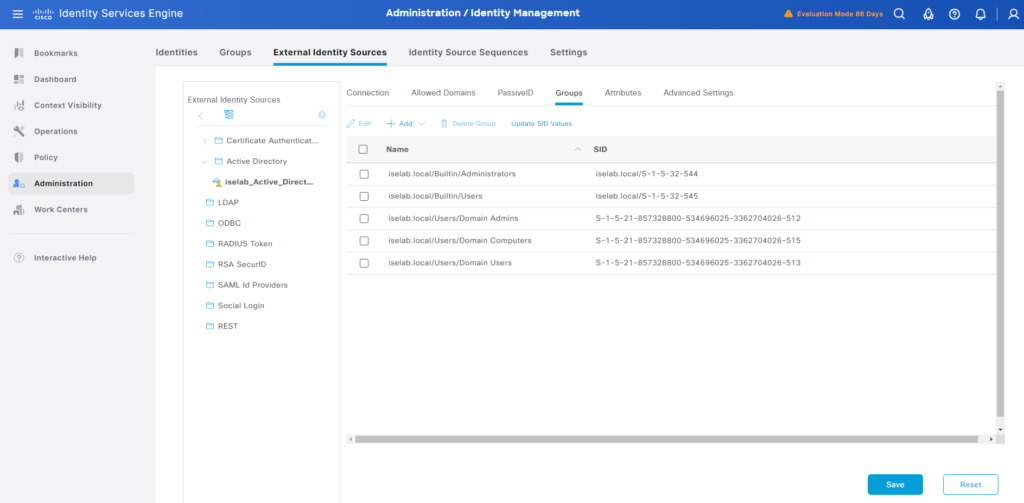
Click Save.
That’s it! We’ve joined AD with ISE and will now be able to query it to for example verify if a user is part of an AD group when writing our authz rules.
Hi Daniel – really enjoying this series of posts!
One point of clarification – the account used to join ISE to AD does not have to be a domain admin. It only needs privileges to search AD, create a machine account and modify that account’s permissions. So, a lesser privileged account can often be used (although a domain admin certainly works).
https://www.cisco.com/c/en/us/td/docs/security/ise/3-4/admin_guide/b_ise_admin_3_4/b_ISE_admin_asset_visibility.html#reference_F19556CAD5C949B58DF89334E2C6255D
Thank you my friend!
That’s good information to have. I have updated the post to reflect this.
Hi Daniel can you please clerify if you are importing OUs or Groups? I think these are different. I don’t have too much knowledge of systems but I think we can’t import OUs from AD and only import Groups?
Yes, you are correct. Sorry for the confusion!