In my ISE lab I’m going to be using EAP-TLS and TEAP, which means I’ll be needing user and computer certificates. The goal is to be able to enable the 802.1X supplicant via GPO and to distribute certificates automatically without requiring any user input. Another post will cover GPO, in this post I’ll cover creating the certificate templates in ADCS.
When opening the CA app, there are a number of templates provided by default:
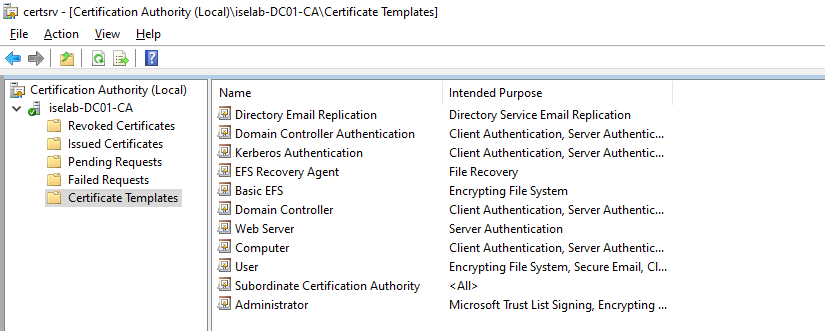
There are already templates for User and Computer, but it’s better to leave the default templates alone and create new ones. First, we’ll create a template for user certificates. Start by right clicking Certificate Templates and selecting Manage:
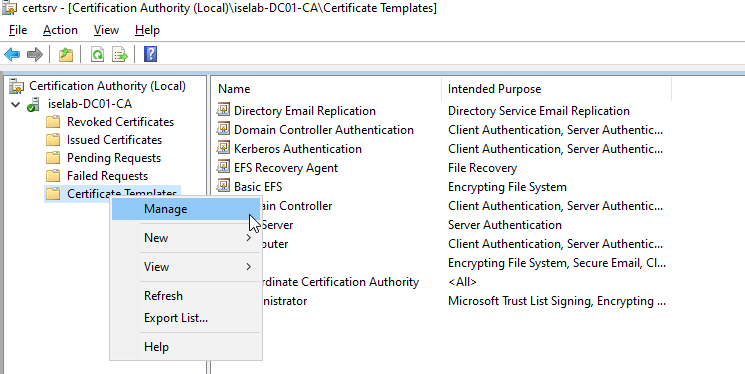
Then we’re going to right click the User template and select Duplicate Template:
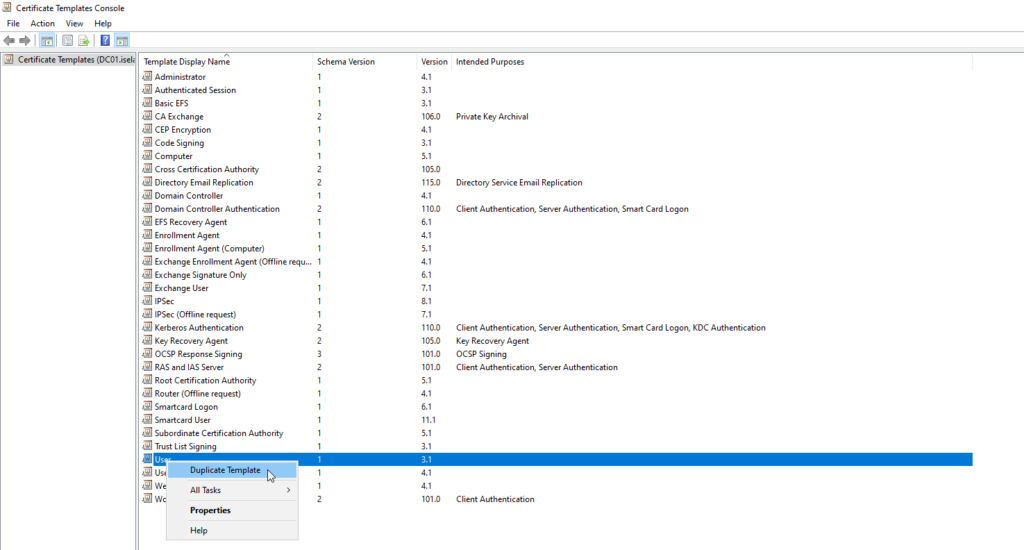
This is going to open up a new window with properties of the template:
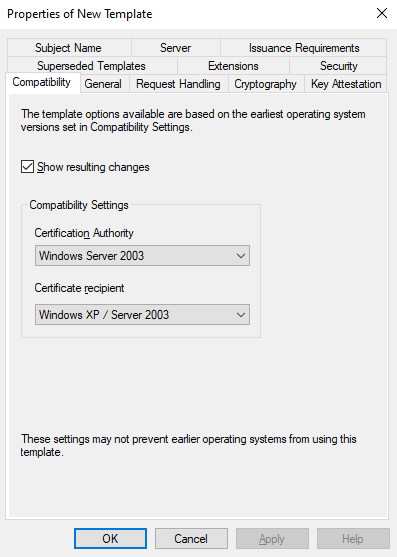
Go to General and give the template a name:
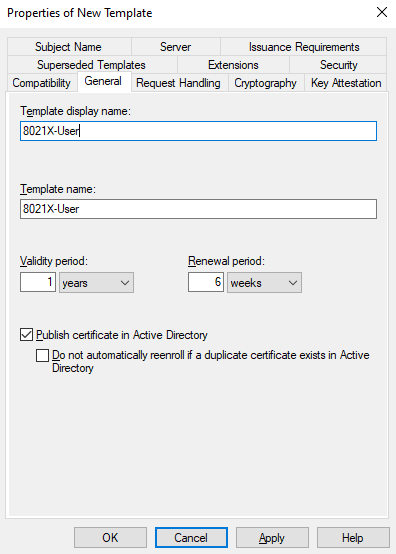
Don’t select the Do not automatically reenroll option or it won’t be possible to renew certs before they expire.
Then go to Request Handling. We’re going to uncheck the Allow private key to be exported option as this is considered more secure:
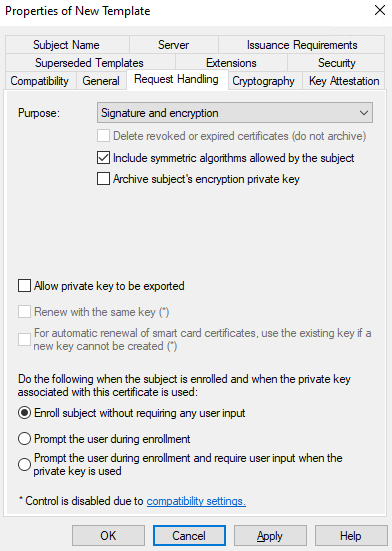
Make sure Enroll subject without requiring any user input is selected. We want to be able to enroll users without them having to provide any information.
Next, go to the Security tab:
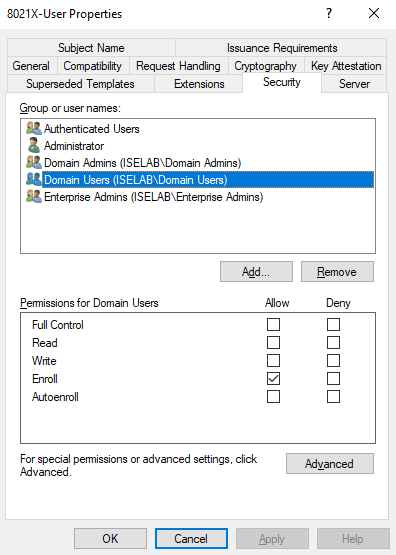
By default, domain users only have enroll privileges, but they need read and autoenroll to be able to autoenroll. Otherwise, the GPO we’ll create later won’t have the expected effect. Add Read and Autoenroll:
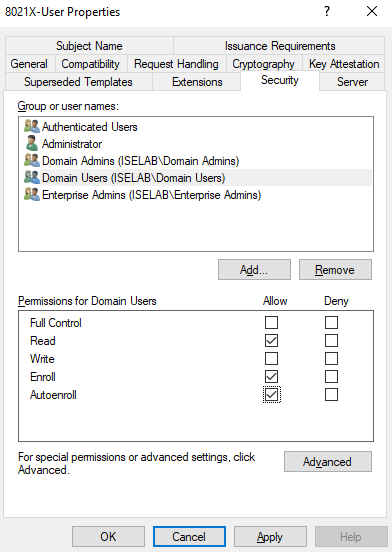
Then go to Subject Name:
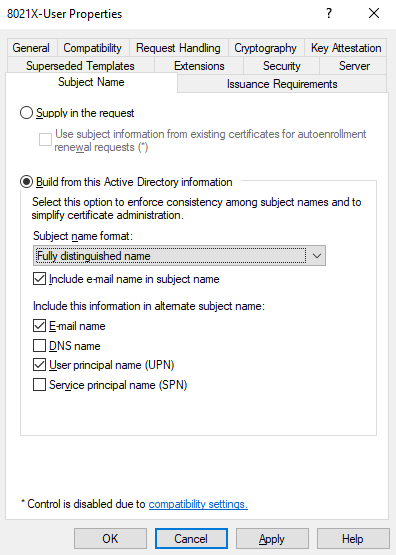
My lab does not have an Exchange server and I’m not going to use the certificate for e-mail so I’m going to deselect Include e-mail name in subject name and E-mail name:
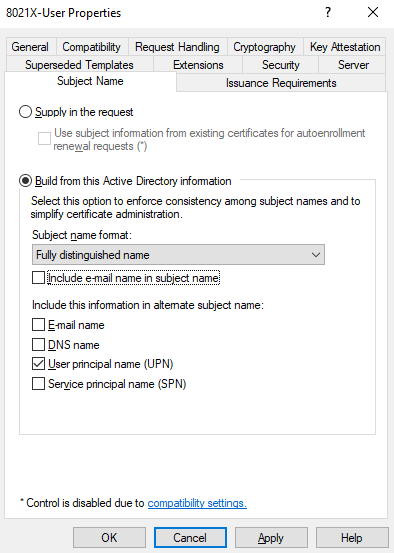
Click Apply and then OK. We’re done with the user certificate template.
Now let’s move on to the computer certificate template. We’ll duplicate the Workstation Authentication certificate template:
Go to the General tab and give the template a name:
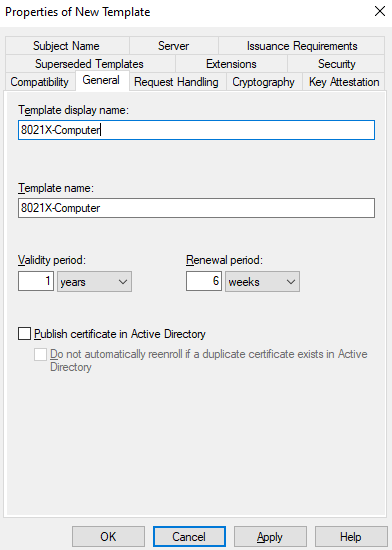
Then go to the Security tab:
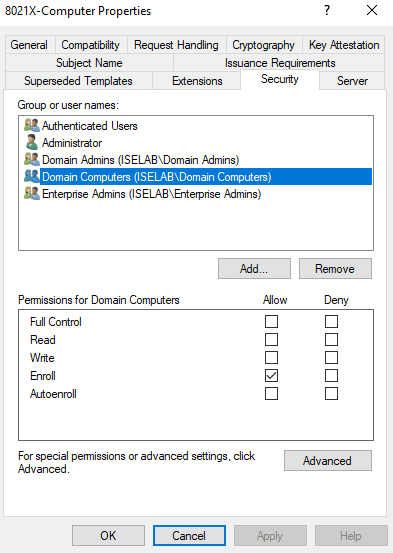
Give Domain Computers privileges to read, enroll, and autoenroll:
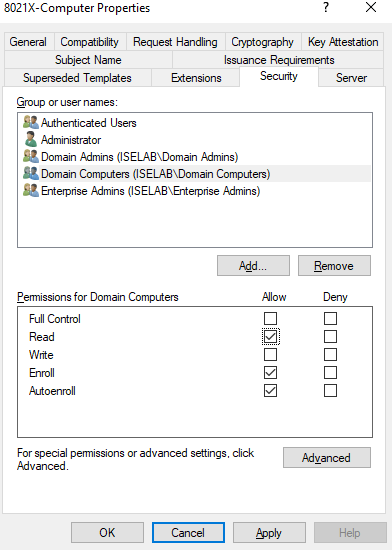
Then go to Subject Name:
I’m going to include User principal name in the SAN and set the Subject name format to Fully distinguished name:
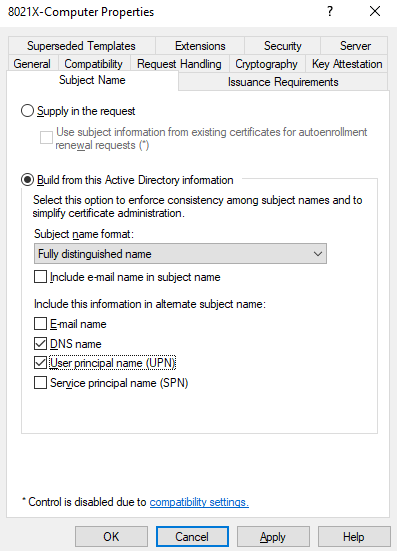
Click Apply and then OK.
Before our new templates can be used, they have to be published. In the CA app, right click on Certificate Templates, select New -> Certificate Template to Issue:
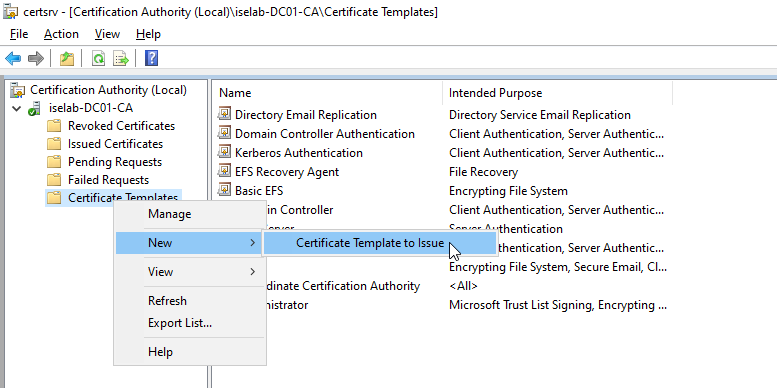
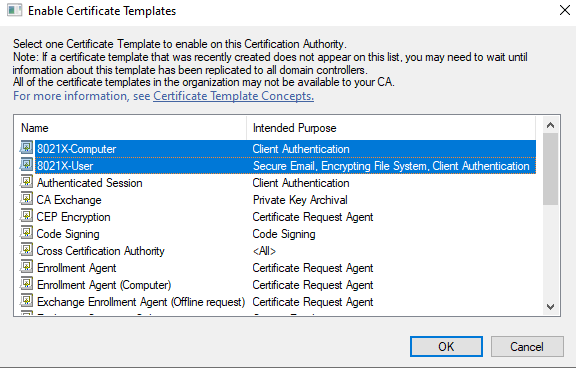
Then select the templates you created (ctrl for multi select) and click OK:
That’s all for this post. In the next post we’ll look at how to use GPO to get users and devices to autoenroll for certificates.
Very useful !
I recently came across and learnt about creating security policies on PaloAlto firewall based on User (user ID) to allow what can this user access or deny what user can’t access. This PC user that is connected to the firewall belongs to the domain configured on AD server which is connected to same network, and its required to configure authentication profile and point towards the AD for user authentication.
Interesting stuff to learn about !